|
|
Every day, people manage many accounts for different reasons, such as logging in to social media, banking sites, computer systems, etc. They share too much personal information on public websites and have a habit of setting the same password across personal and business accounts because it is easy to remember. This practice is common enough to enable an attacker to guess passwords or extract a company’s confidential information. Attackers often rely on various types of password attack techniques (Phishing, Brute Force, Keyloggers, etc.) to crack credentials easily and break into a system. The following discussion focuses on the Brute Force password attack technique, how it works, and detecting and preventing such password attacks.

What is a Brute Force Attack?
A brute force attack is a trial-and-error technique attackers use to discover valid user credentials by guessing every possible combination of characters until they find the correct combination. Attackers target credentials to steal sensitive information or conduct malicious operations on the targeted systems. They rely on the Brute Force attack technique because there is a high chance of gaining access to user accounts. With the right credentials to match, they can compromise any endpoint on the network and move laterally to other systems.
Types of Brute Force Attacks
Password Guessing – An attacker may guess login credentials without prior knowledge of system or environment passwords during an operation by using a list of common passwords.
Password Cracking – The process can involve comparing a list of words to guess passwords or using an algorithm to guess the password repeatedly. Attackers can use a pre-computed dictionary of plaintext passwords and their corresponding hash values to determine what plaintext password produces a particular hash.
Password Spraying – In this low-and-slow technique, attackers use a single or small list of commonly used passwords, such as those found on the internet against a single user account.
Credential Stuffing – Attackers automate login requests against a web application. They use previously discovered credential pairs(usernames/email addresses and passwords) to gain unauthorized access. A survey by SecureAuth found that 81% of users have reused a password across two or more sites, and 25% of users use the same passwords across most of their accounts.
How Brute Force Attacks Work
Let’s see how brute force attack works now. Attackers have a handful of readily and freely available tools (such as Metasploit, John the Ripper, Hydra, etc.).
Most of the time, attackers use automated tools or scripts with a list of usernames and passwords. The tool will automatically send the combination of these usernames and passwords to the targeted system, such as a web application server. The tool will check if the authentication is successful or not.
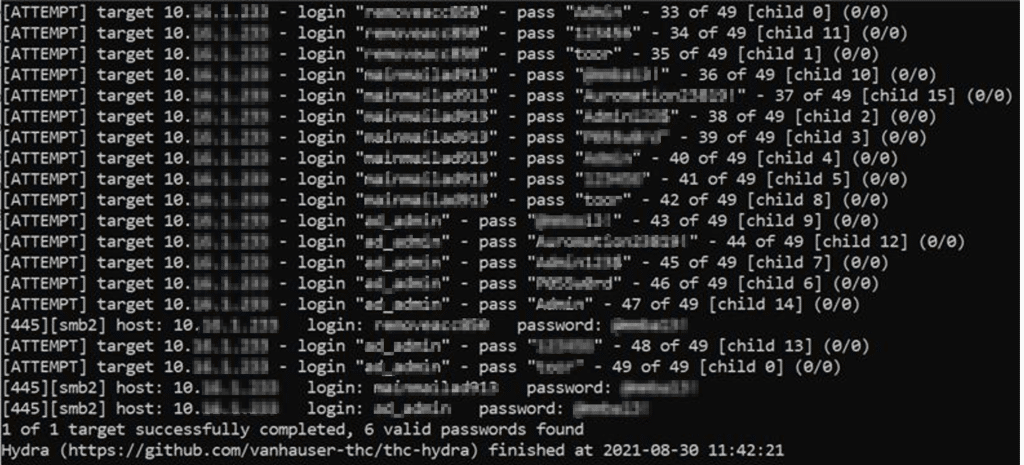
Here is a screenshot of the Hydra tool launching a brute force attack and the valid passwords found against the targets.
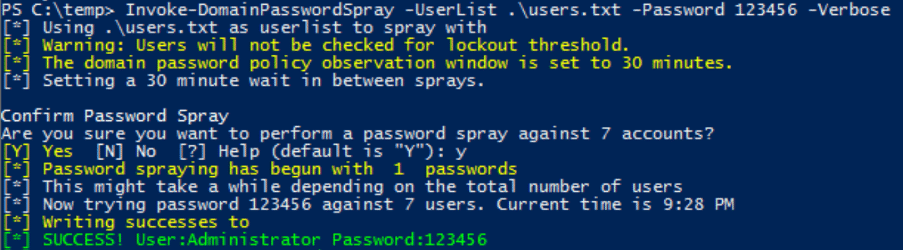
Here is another screenshot of the “DomainPasswordSpray” tool.
Another post-exploitation tool called CrackMapExec (CME) targets Active Directory user accounts to conduct lateral movement. The CME can also brute force passwords for a specified user on a single target system or across an entire network. The following examples show how attackers use CME to brute force credential authentication by using a supplied list of usernames and a single password.
Examples:
<code>crackmapexec 10.0.100.0/24 -u ‘admin’ -p ‘P@s$w0Rd’</code>
<code>crackmapexec <protocol> <target(s)> -u username1 username2 -p password1</code>
<code>crackmapexec <protocol> <target(s)> -u ~/file_usernames -p ~/file_passwords</code>
The remote desktop protocol (RDP) brute force attack is one of the most common methods attackers use to gain access to Windows workstations or servers. This method is so successful that ransomware groups have used open RDP ports to deliver malware payloads.
How to Prevent a Brute Force Attack?
The first step in preventing brute force attacks is to ban the use of common passwords, such as 123456, qwerty, password, and 123123. There are complete lists of common passwords for reference to create a ban list. Security administrators can implement security standards for creating passwords. For example, the list should include, but is not limited to:
- Avoid the use of repetitive or sequential characters (example aaaaaa, 1234abcd).
- Always use the combination of alphanumeric characters and symbols.
- Never use personal identification information(date of birth, surname, etc.)
In addition to the above, following best practices can also make it difficult for attackers to guess or crack passwords through brute force attacks:
- Enforce the use of strong and complex passwords.
- Make sure you use a unique password for each account.
- Reset passwords every three months.
- Configure the Account Lockout policy.
- Use Captcha.
- Use Two Factor Authentication (2FA).
- Periodically conduct Active Directory assessments.
Detection and Defensive Strategy
Attackers often discover password policies to create a list of common passwords and launch dictionary or brute force attacks that adhere to the policy. Our Ranger® Identity Assessor for AD solution performs a continuous assessment of Active Directory and provides real-time detection of brute force or password spray attacks. Our SingularityTM Identity solution deploys deceptive credentials on production endpoints, detecting when attackers compromise deceptive credentials and redirecting them to decoys systems for engagement. Any brute force attempt using deceptive credentials generates an alert as a stolen credentials attack.
Conclusion
Organizations can’t prevent password attacks, but they can avoid them. Attackers can build credential matches after launching brute force attacks against their targets, exploiting weak passwords and open RDP ports. Gaining access to more AD accounts in the organization is much more vulnerable, leading to privilege escalation or lateral movements. Organizations can enforce strong password policies that can protect from brute force attacks.
Share on:
References
The Center for Internet Security (CIS) Password Policy Guide
NIST 800-63B: Digital Identity Guidelines



