|
|
A previous blog on detecting unconstrained delegation exposure showed a typical attack scenario with Kerberos authentication. It also discussed how an attacker could discover domain computers with an unconstrained delegation and abuse Kerberos TGTs (ticket-granting tickets) to achieve their goals.
This blog post explores the Kerberoasting Technique and how ticket-granting service (TGS) tickets can be vulnerable to Brute Force attacks. It also discusses Kerberos security policy settings and the vulnerable misconfigurations an attacker might exploit.
Active Directory Kerberos Attacks
Attackers often target Microsoft’s Kerberos implementation in Active Directory (AD). There are several Kerberos attacks such as SPN Scanning, Kerberoasting, Silver Tickets, and Golden Tickets. Among all these popular attacks, Kerberoasting is an effective method that an attacker uses to extract service account credentials from AD.
Before digging deeper into Kerberoasting attacks and how they work, one should understand why attackers are most interested in service accounts.
- Service account passwords are of the same length, and they do not expire.
- Most service accounts have elevated permission and are often members of highly privileged groups like Domain Admins providing full admin rights to AD.
- Cracking the service account passwords enables attackers to exploit the Kerberos mechanism and compromise the entire AD domain.
What is Kerberoasting?
The Kerberoasting technique is an effective method for extracting service account credentials from AD as a regular user without sending any packets to the target system. In this technique, an attacker can abuse a valid Kerberos ticket-granting ticket (TGT) or sniff network traffic to obtain a ticket-granting service (TGS) ticket that may be vulnerable to Brute Force attacks.
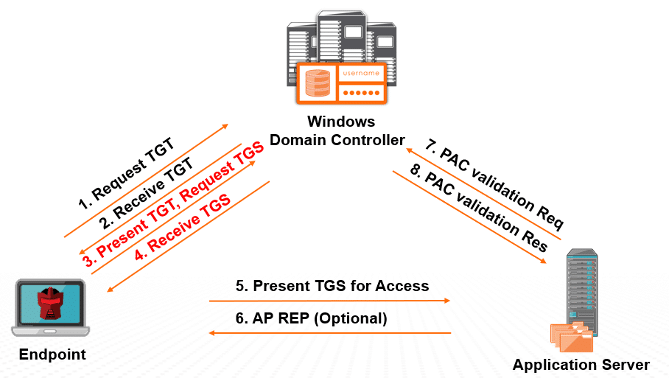
Attackers use the following process to crack a vulnerable service account password offline.
The first step is to discover Service Principal Names (SPNs). Attackers can easily find all SPNs of specific types using the Active Directory PowerShell module. The most useful SPN type that an attacker scan for is “SQL”. For example, the Get-ADObject cmdlet shown below discovers all SQL servers registered in Active Directory.
“get-adobject -filter {serviceprincipalname -like “*sql*”} -prop serviceprincipalname”
As shown in the figure below, an attacker presents a valid domain user’s authentication ticket (TGT) to request one or more Kerberos ticket-granting service (TGS) tickets for any Service Principal Name (SPN) from a domain controller (DC). Attackers take advantage of Microsoft’s legacy support for Kerberos RC4 encryption (RC4_HMAC_MD5) since the NTLM password hash is used extensively with this encryption type. When requesting TGS tickets, attackers can force them to use RC4 encryption.
After identifying the target server, the attacker gets the list of SPNs associated with service accounts. They can use these service accounts to request Kerberos TGS service tickets from a domain controller (DC).
“Add-Type -AssemblyName System.IdentityModel”
“New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList “<MSSQLSvc/HOST:PORT>””
Note: The service ticket requested using the open-source tool Mimikatz has the RC4 encryption type.
Once the client receives the ticket, an attacker can export all Kerberos service tickets from the user’s memory to a file without elevated rights. The attacker sends the exported service ticket to the attacking machine to brute force for offline cracking.
Mitigations
Organizations can implement the following best practices to prevent the entire domain from getting compromised as a mitigation strategy.
- Make sure all service accounts have long, complex passwords (greater than 25).
- Change service account passwords regularly (at least once a year).
- Use group managed service accounts (gMSAs) that provide passwords management and eliminate the need for an administrator to manage each service account’s credentials manually.
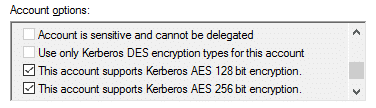
- MITRE ATT&CK also recommends enabling AES Kerberos encryption (or another stronger encryption algorithm) rather than RC4, making it difficult for attackers to crack hashes offline. Enable the AES 128/256-bit encryption type using the checkboxes in the Account tab.
Kerberos Security Policy Settings and Recommendations
Organizations should pay close attention to the Kerberos policy settings to reduce the risk of attackers stealing credentials. These policy settings are under Computer ConfigurationWindows SettingsSecurity SettingsAccount PoliciesKerberos Policy.
An attacker can explore vulnerable policy settings to exploit them. The following are Kerberos security policy settings and recommended options.
- Enforce user logon restrictions – If this policy setting is disabled, users might get session tickets for services they do not have the right to use. The recommendation is to set this policy to “Enabled”.
- Maximum lifetime for service ticket – This policy determines the maximum number of minutes to use a granted session ticket to access a particular service.
The recommendation is to set this policy to 600 minutes. Configuring too high a value for the “Maximum lifetime for service ticket” might allow users to access network resources outside their logon hours. Also, disabled user accounts might continue to access network services with valid service tickets issued before their accounts were disabled.
- Maximum lifetime for user ticket – This policy determines the maximum amount of time (in hours) to use a user’s ticket-granting ticket. When a user’s ticket-granting ticket expires, the system must request a new one or renew the existing one. The recommendation is to set this policy to 10 hours. Configuring too high value might allow users to access network resources outside of their logon hours. Also, disabled user accounts might continue to have access to network services with valid user tickets issued before their accounts were disabled. Configuring too low a value might affect the Key Distribution Center (KDC) performance in requesting tickets and result in a DoS attack.
- Maximum lifetime for user ticket renewal – This policy setting determines the period (in days) to renew a user’s ticket-granting ticket. The recommendation is to set this policy to 7 days. Configuring too high a value might allow users to renew very old user tickets.
- Maximum tolerance for computer clock synchronization – This policy setting determines the maximum time difference (in minutes) that Kerberos V5 tolerates between the time on the client clock and the time on the domain controller that provides Kerberos authentication. The recommendation is to set this policy to a value of 5 minutes.
Attivo Networks Solutions
Setting the right Kerberos policy is extremely important for an organization. A weak or misconfiguration of Kerberos policy can lead to complete AD domain compromise. The Attivo Networks ADAssessor continuously monitors Active Directory for vulnerabilities. The ADSecure solution detects Kerberos ticket enumeration and triggers events on potential Kerberoasting attacks.
The Endpoint Detection Net (EDN) Suite ThreatStrike® module deploys deceptive credentials, including hashes, authentication tokens, and Kerberos tickets. The solution also helps to detect attackers using deceptive tickets and redirects them to decoys systems for engagement.
Conclusion
Many organizations provision service accounts with too many permissions, often with weak passwords, making an easy way for an attacker to go from domain user to domain admin. Implementing continuous assessment and validating Kerberos configurations can avoid being vulnerable to privilege escalations and lateral movement.
References
- Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain
- Steal or Forge Kerberos Tickets



