|
|
A pair of zero-day vulnerabilities in Google Chrome (CVE-2020-15999) and Microsoft Windows (CVE-2020-17087) are being chained together and exploited to perform privilege escalation and gain administrator access to a system.
CVE-2020-15999 involves a type of memory-corruption vulnerability called a heap buffer overflow in Freetype, a popular open-source software development library for rendering fonts included with standard Chrome distributions.
CVE-2020-17087 involves the Windows Kernel Cryptography Driver (cng.sys) exposing a DeviceCNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures. It constitutes a locally accessible attack surface that attackers can exploit for privilege escalation (such as sandbox escape).
Attackers can chain together CVE-2020-15999 and CVE-2020-17087, which allows them to escalate system privileges and break out of the Chrome sandbox. Security researchers have published POC code to exploit CVE-2020-15999 as well.
By far, Google Chrome is the most popular browser, and there are reports that an exploit for CVE-2020-15999 exists in the wild. Attackers, once they obtain a footprint on compromised endpoints with administrative privileges, can install additional tools, turn off services or quickly map and enumerate the network. To limit suspicious activity and possible detection, the actors choose to use living-off-the-land techniques and, if possible, native tools such as listed below to identify high-value assets in the network
- nltest – to discover domain controllers
- net group /domain – to perform domain enumeration
- net localgroup – to discover local administrators
- setspn – to discover service principles
- net use, net share – to discover SMB shares
- ADSI (Active Directory Service Interface) to enumerate Active Directory
- File discovery to locate possible SSH keys, Cloud keys, etc.
Here are some of the common MITRE techniques used by attackers after gaining an initial foothold
T1087: Account Discovery
T1083: File and Directory Discovery
T1069: Permission Groups Discovery
T1482: Domain Trust Discovery
T1135: Network Share Discovery
T1018: Remote System Discovery
T1016: System Network Configuration
T1087: Valid Accounts
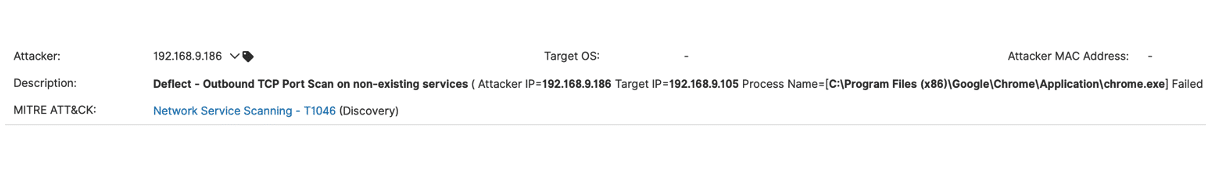
T1046: Network Service Scanning
T1555: Credentials From Password Stores
Now more than ever, it is critical for organizations to protect their endpoints and prevent attackers from spreading throughout the network. The Attivo Networks® Endpoint Detection Net (EDN) prevents attackers from breaking out from an infected system by restricting their ability to conduct reconnaissance or move laterally.
The following use cases highlight the capabilities that are part of the EDN suite.
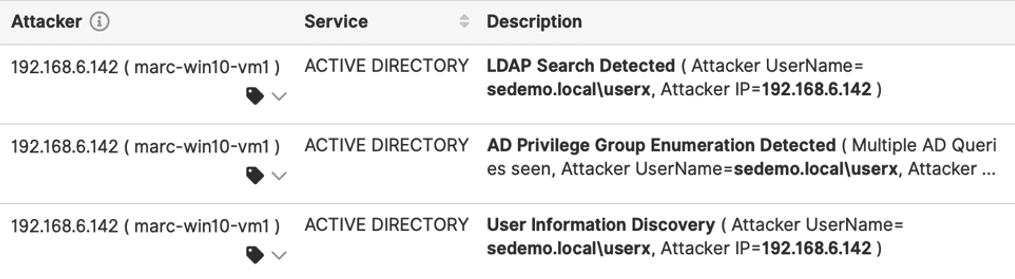
- Protects from attackers targeting and discovering permissions in Active Directory.
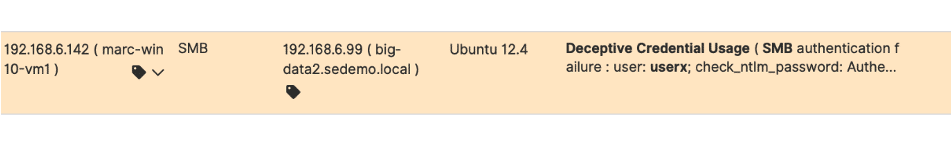
- Detects attackers stealing credentials from compromised endpoints.
- Prevents attackers from moving laterally using mapped network shares
- Detect and redirect attackers performing network reconnaissance
EDN Protection Best Practices:
- Deploy ADSecure on all windows endpoints which can access domain controllers
- Deploy deceptive breadcrumbs on all users’ endpoints, production workloads on-premise, or in the cloud and containers.
- Deploy “Deflect” to detect and alert attackers’ network reconnaissance attempts
EDN Domain Reconnaissance Visibility:
EDN Credential Theft Visibility:
EDN Network Reconnaissance Visibility:
 Additional Resources:
Additional Resources:
- Learn how to protect against targeted Active Directory Ransomware attacks.
- Learn how to prevent lateral movement using SMB session enumeration.



