|
|
Adversaries are adopting creative methods in these COVID-19 epidemic conditions to gain access to company assets. Ransomware is one such creative digital form of extortion that affects companies of all sizes. One prevalent method adversaries use to compromise and deploy ransomware to multiple systems is using a single management server in the organization.
Most IT administrators have heard of and used Microsoft’s System Center Configuration Manager (SCCM), now known as the Microsoft Endpoint Manager. Organizations use SCCM to deploy Windows Operating System patches, software updates, and 3rd party Applications automatically. The endless capabilities available to manage endpoints with SCCM makes it must-have software in an enterprise. While the SCCM management server makes an IT administrator’s job easy, an adversary could take it over and use it to deploy malware and ransomware to all endpoints if one does not protect it appropriately. The following article offers good insight into how Red or Purple teams can incorporate SCCM servers into their testing.
What actions should a security administrator take to protect SCCM Infrastructure?
The first step in protecting the SCCM infrastructure is to prevent the adversaries from enumerating Active Directory and identifying privileged users, groups with Discovery Process rights, and SCCM servers. SCCM enables administrators to manage the security and deployment of applications and devices that are part of any organization. SCCM, along with Active Directory, helps manage all the systems and accounts stored in the database. SCCM has a discovery process that queries for the Users, Computers (Client & Servers), and maintains a user device affinity that tells each machine to which user it belongs. Any privileged users in AD can also be an SCCM administrator, and any Domain users can query AD to understand the SCCM infrastructure or configuration.
The following attack sequence discusses how adversaries can compromise an endpoint joined to the domain. Once inside the network, adversaries must find privileged users to elevate themselves. Domain-joined windows endpoints allow any user to query Active Directory without any additional privileges, making it easy for adversaries to gather the information. In just a few steps, they can elevate themselves as Domain Admins, compromise an SCCM Server, and deploy ransomware on many systems.
- Enumerate Local Administrators Group
- Command net localgroup Administrators
- Enumerate the AD Group from the previous step
- Command: net group ‘Local Admin Group’ /Domain
- Determine if the logged-on user is a member of the Local Admin group
- Command: whoami /all
- Find a Domain Controller
- Command: nltest /dsgetdc:<Domain Name>
- Find Domain Admins
- Command: net group “’Domain Admins’ /Domain”
- Find Sessions for Domain Admins from the previous step
- Command: exe <Domain Controller IP or Name>
- Find any Domain Admins from the previous step
- Command: Net Group ‘Domain Admins’ /Domain
- Move laterally to the system identified in the previous step
- Command: psexec computername cmd
- Find SCCM servers and SCCM Admins using an LDAP query
- Command: adfind -f (&(objectcategory=group)(name=*sccm*))
- RDP to the SCCM server
- Command: mstsc /v:<SCCM server name>
- Deploy ransomware through SCCM
In 11 Steps, they can compromise an SCCM Server from a single Windows endpoint. All of this was possible because the adversary could gather information from Active Directory using native commands. Typical security tools don’t detect these operations as they are all standard built-in commands IT administrators use for their day to day tasks. To prevent such attacks against the SCCM and Active Directory environments, one needs a solution that understands Active Directory.
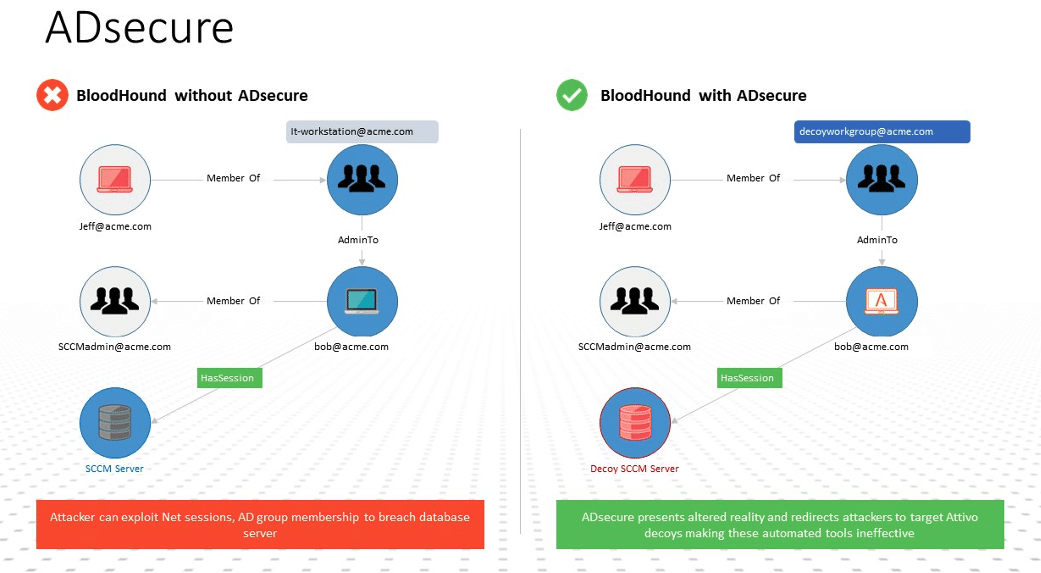
The Attivo Networks Endpoint Detection Net (EDN) suite’s ADSecure solution is an innovative security product that protects Active Directory against unauthorized reconnaissance. Unlike other security tools that merely detect and report, with the ADSecure solution, organizations gain Active Directory (AD) security without interfering with production Domain Controllers. The solution identifies unauthorized AD queries and returns fake object information to misdirect attackers into a decoy environment. The mere act of attacker observation triggers an alert on unauthorized activity, while the deceptive objects serve to disrupt automated attack tools. Additionally, the solution gathers Tactics, Techniques, and Procedures (TTPs) and company-specific threat intelligence to accelerate incident response. It provides real-time alerting while disrupting the activities and denying attacker access to Active Directory information they could leverage to continue their attack.
Want to try our innovative solution for yourself? Register for a 30 Day Trial.



