RangerAD
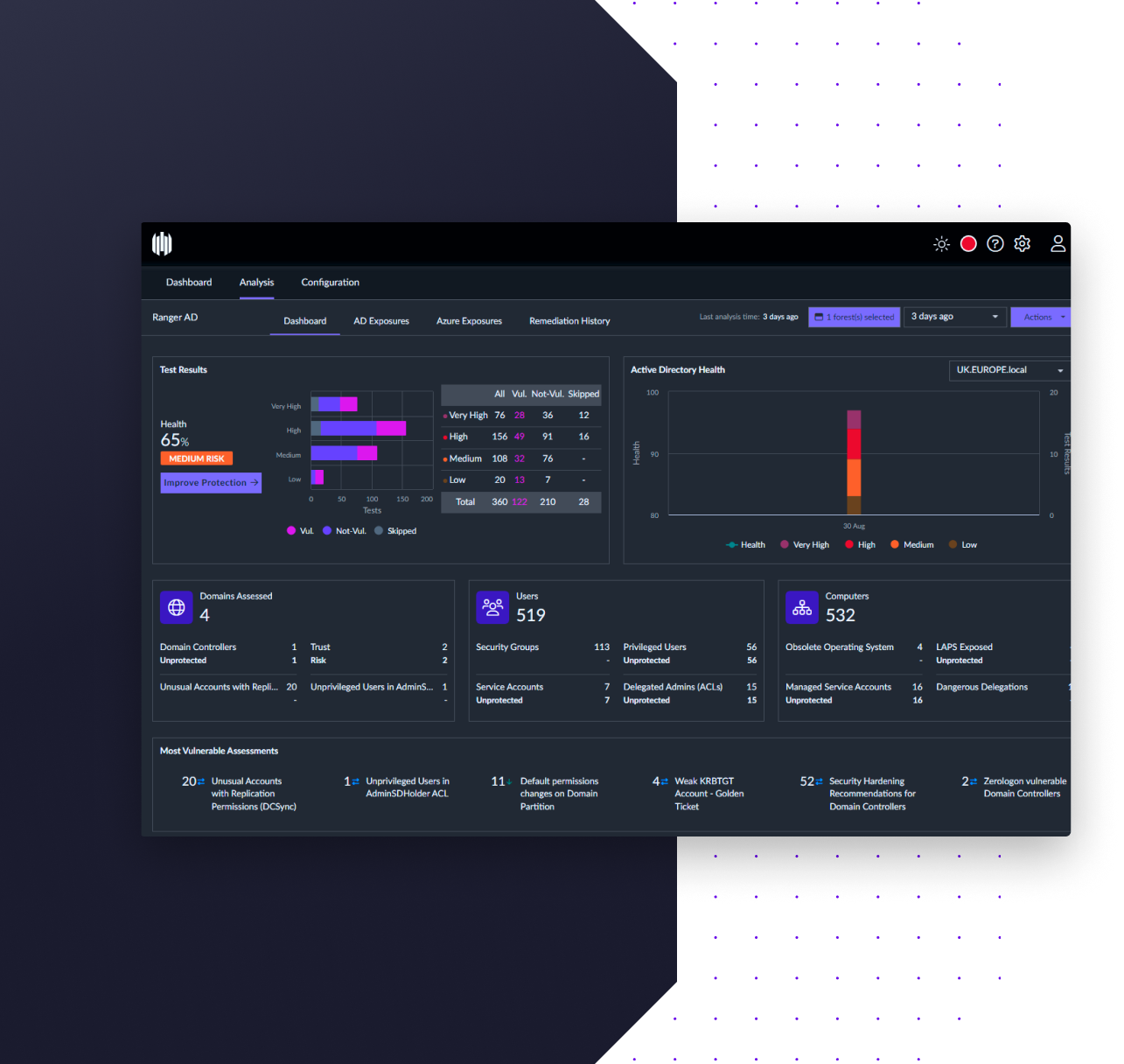
Ranger AD continuously identifies critical domain, computer, and user-level exposures in Active Directory and Azure AD, and even monitors for potential active attacks. Easily take action on those risks with prescriptive remediation guidance.